
Bots are good at guessing usernames and trying to brute force into your WP installation by guessing your password.
It’s not just accounts like ‘admin’ and ‘yourdomainame’ either. No matter how well you try to hide your login username, there are plenty of places it can leak out where bots can find it.
Wordfence has a nifty feature to block anyone logging in with a username that doesn’t exist in the WP users table, however, once a bot has your real username, they can keep trying to guess the password until Wordfence blocks them. If you are not using any kind of login protection, they can keep trying until they crack the password.
Here are some basic practices for securing your username and login.
Basic practice #1: 2FA
It’s recommended to use 2FA anywhere possible. This will really tighten up your login security and is a feature in the Wordfence plugin (Dashboard > Wordfence > Login Security). 2FA requires an app on your phone that displays a timed code. When logging into your site, you simply open the app and type in the code into the login field.
2FA can really slow you down and can be a pain for regular users, however, the benefits far outweigh the drawbacks and after an adjustment period, your site users will log in easily.
Also, 2FA has become standard in many other apps and is more widely known than before so it’s likely your users already have an app.
Basic Practice #2: Obfuscate
Make your login username hard to guess. It’s not always practical to just have a password-like username as well as a strong password, but for example ‘user727d68’ is much harder to guess than ‘user’.
Basic Practice #3: No Common Names
Do not use common usernames such as admin, editor, author, etc. Your username should also not be the same as your domain name. So for example youracesite.com should not have a username ‘youracesite’. You should also avoid combinations such as ‘firstnamelastname’ from information easily identifiable on your website. These are the first usernames bots will try on your site when attacking.
Basic Practice #4: Information Leakage
There are a few places in WP where your username/user info is on display.
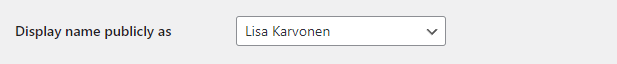
The first is the display name field on your user profile (Dashboard > Users > Profile). Your display name should be different from your username. This display name is shown on the author bio and possibly on single-page templates etc.
Another place that leaks information is Yoast’s Author Archives which links to your author sitemap using your real login username. You can either turn off Yoast Author Archives or use this handy little plugin to rename your author slug. More information on this issue can be found (from 2019 already..) here.
Basic Practice #5: Blocking Brute Force Attacks
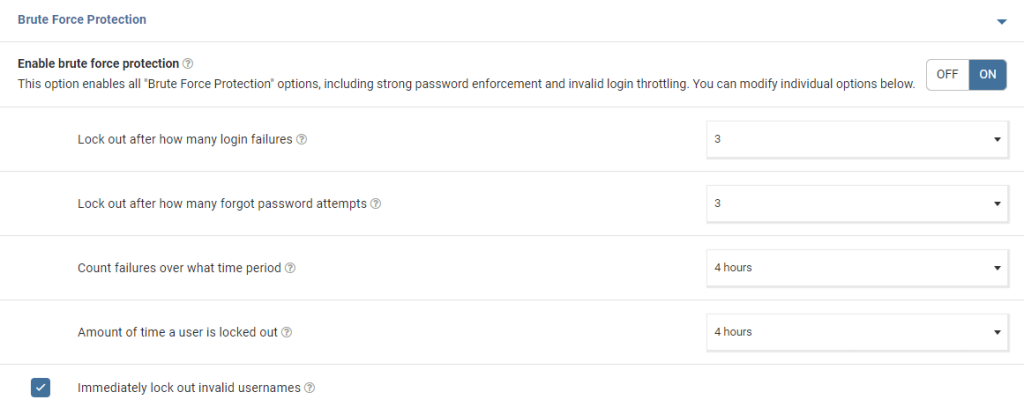
By making sure that Wordfence is set up to block incorrect usernames and limit login attempts, you are already one step ahead of the game. It’s still good to keep in mind though, that you can help those tools protect your site better by following some basic security practices within your blog. Security tools can only help you so far if your login credentials are weak.
Basic Practice #6: Monitoring Brute Force Attacks
Wordfence keeps a good log of login attempts and failures. If you keep track of these attempts, you can see whether any bots are trying to brute force your real username. If they are, then you can change your username (usually needs changing straight in the DB).
Monitoring what’s happening on your site doesn’t need to be a full-time job. By following some basic practices you can tighten security and your data. Feel free to contact us if you have any questions about how our platform can secure your site, or check out our free course to learn how to secure your site yourself.
Photo by Patrick Tomasso on Unsplash.




